

Course 8 - Protecting Against Risks
After you identify what you must protect, you must develop and implement appropriate safeguards for those items to keep them as secure as possible.
Protecting includes providing barriers to anyone seeking to access your digital and physical assets without proper authorization to do so, establishing processes and procedures to protect your sensitive data.
Defending your perimeter is essentially the digital equivalent of building a moat around a castle- and attempting to stop anyone from entering.
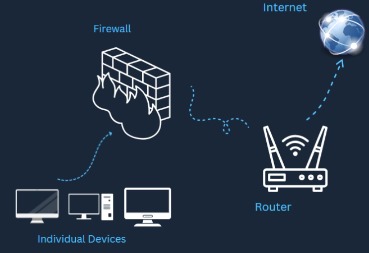
You can build that digital moat by never connecting a computer directly to your Internet modem. Instead, connect a firewall/router to the modem and connect computers to the firewall/router.
Side Note: A modem is a network device that connects your devices to the internet. It does this by converting digital data signals into analog signals that can be transmitted over phone lines.
Modern routers used in home environments include firewalling capabilities that block most forms of inbound traffic. A firewall blocks outsiders from trying to contact a computer inside your home, but it will not block a web server from responding if a computer inside your home requests a web page from the server.
One important technology is Network Address Translation (NAT), which allows computers on your home network to use Internet Protocol (IP) addresses that are invalid for use on the internet, but can be used on private networks. To the internet, all devices on networks using NAT appear to use one address, which is the address of the firewall that is situated between them (the devices) and the Internet. This gives increased protection, as attacks won’t get the specific IP address for your individual device.
Control physical access to your computer and keep it in a safe location
If possible, do not share your computer with family members
Do not rely on deleting data before throwing out, recycling, donating, or selling an old device. (Use a multiwipe erasure system for all hard drives and solid-state drives. Ideally, remove the storage media from all computers before getting rid of the device.)